Sometimes in event of ddos attack the firewall sessions can reach the maximum limit which might cause the intermittent access to the server.
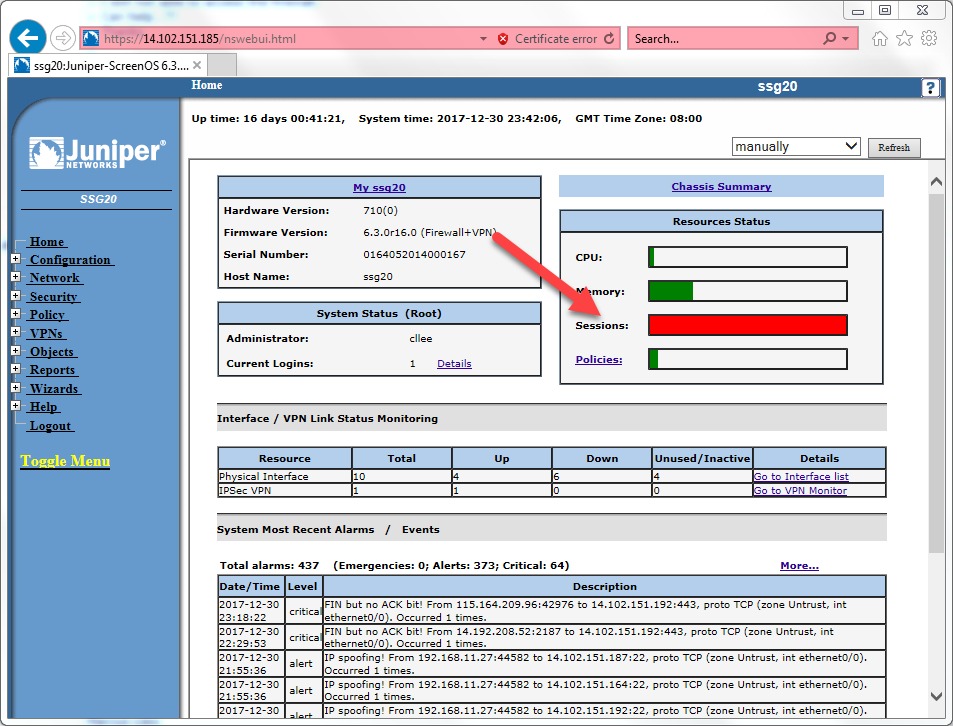
In order to clear the sessions please perform the steps below:
1. SSH to the firewall
2. Check on the current sessions:
Remote Management Console
ssg20->
ssg20-> get session
alloc 7996/max 8064, alloc failed 87563, mcast alloc 0, di alloc failed 0
total reserved 0, free sessions in shared pool 8021
id 17/s**,vsys 0,flag 00000040/0000/0001/0000,policy 4,time 4, dip 0 module 0
if 20(nspflag 2801):192.168.2.74/51037->192.168.9.10/389,17,000000000000,sess token 4,vlan 0,tun 40000002,vsd 0,route 7
if 9(nspflag 800800):192.168.2.74/51037<-192.168.9.10/389,17,000c293511e7,sess token 3,vlan 0,tun 0,vsd 0,route 3
id 222/s**,vsys 0,flag 00000040/0000/0001/0000,policy 4,time 6, dip 0 module 0
if 20(nspflag 2801):192.168.2.203/58078->192.168.9.10/389,17,000000000000,sess token 4,vlan 0,tun 40000002,vsd 0,route 7
if 9(nspflag 800800):192.168.2.203/58078<-192.168.9.10/389,17,000c293511e7,sess token 3,vlan 0,tun 0,vsd 0,route 3
id 392/s**,vsys 0,flag 04000000/0000/0001/0000,policy 1,time 55, dip 0 module 0
if 9(nspflag 800801):192.168.9.20/61265->23.58.230.170/443,6,000c29b0babc,sess token 3,vlan 0,tun 0,vsd 0,route 3,wsf 5
if 0(nspflag 800800):14.102.151.191/61265<-23.58.230.170/443,6,00005e000123,sess token 4,vlan 0,tun 0,vsd 0,route 5,wsf 8
id 654/s**,vsys 0,flag 00000040/0000/0001/0000,policy 4,time 1, dip 0 module 0
if 20(nspflag 2801):192.168.2.203/57952->192.168.9.10/389,17,000000000000,sess token 4,vlan 0,tun 40000002,vsd 0,route 7
if 9(nspflag 800800):192.168.2.203/57952<-192.168.9.10/389,17,000c293511e7,sess token 3,vlan 0,tun 0,vsd 0,route 3
id 797/s**,vsys 0,flag 00000040/0000/0001/0000,policy 4,time 1, dip 0 module 0
if 20(nspflag 2801):192.168.2.203/58010->192.168.9.10/389,17,000000000000,sess token 4,vlan 0,tun 40000002,vsd 0,route 7
if 9(nspflag 800800):192.168.2.203/58010<-192.168.9.10/389,17,000c293511e7,sess token 3,vlan 0,tun 0,vsd 0,route 3
id 1019/s**,vsys 0,flag 04000000/0000/0001/0000,policy 8,time 13107, dip 0 module 0
if 0(nspflag 800801):172.68.58.97/14193->14.102.151.191/80,6,00005e000123,sess token 4,vlan 0,tun 0,vsd 0,route 5,wsf 8
if 9(nspflag 800800):172.68.58.97/14193<-192.168.9.20/80,6,000c29b0babc,sess token 3,vlan 0,tun 0,vsd 0,route 3,wsf 10
id 1217/s**,vsys 0,flag 00000040/0000/0001/0000,policy 4,time 6, dip 0 module 0
if 20(nspflag 2801):192.168.2.203/58103->192.168.9.10/389,17,000000000000,sess token 4,vlan 0,tun 40000002,vsd 0,route 7
if 9(nspflag 800800):192.168.2.203/58103<-192.168.9.10/389,17,000c293511e7,sess token 3,vlan 0,tun 0,vsd 0,route 3
id 1228/s**,vsys 0,flag 00000000/0000/0001/0000,policy 1,time 27, dip 2 module 0
3. Clear the sessions:
ssg20-> clear session all
Total cleared software sessions :7996
4. Check back on the sessions status- the number of sessions should reduce: